
Cranes rest idle while waiting for a ship to dock to remove cargo containers in Los Angeles Harbor on March 14, 2024.
- U.S. physical infrastructure is increasingly the target of hacks, with Google's cybersecurity firm Mandiant releasing a report Wednesday teasing out links between Russian hackers and a January attack on a water filtration plant in a small Texas town.
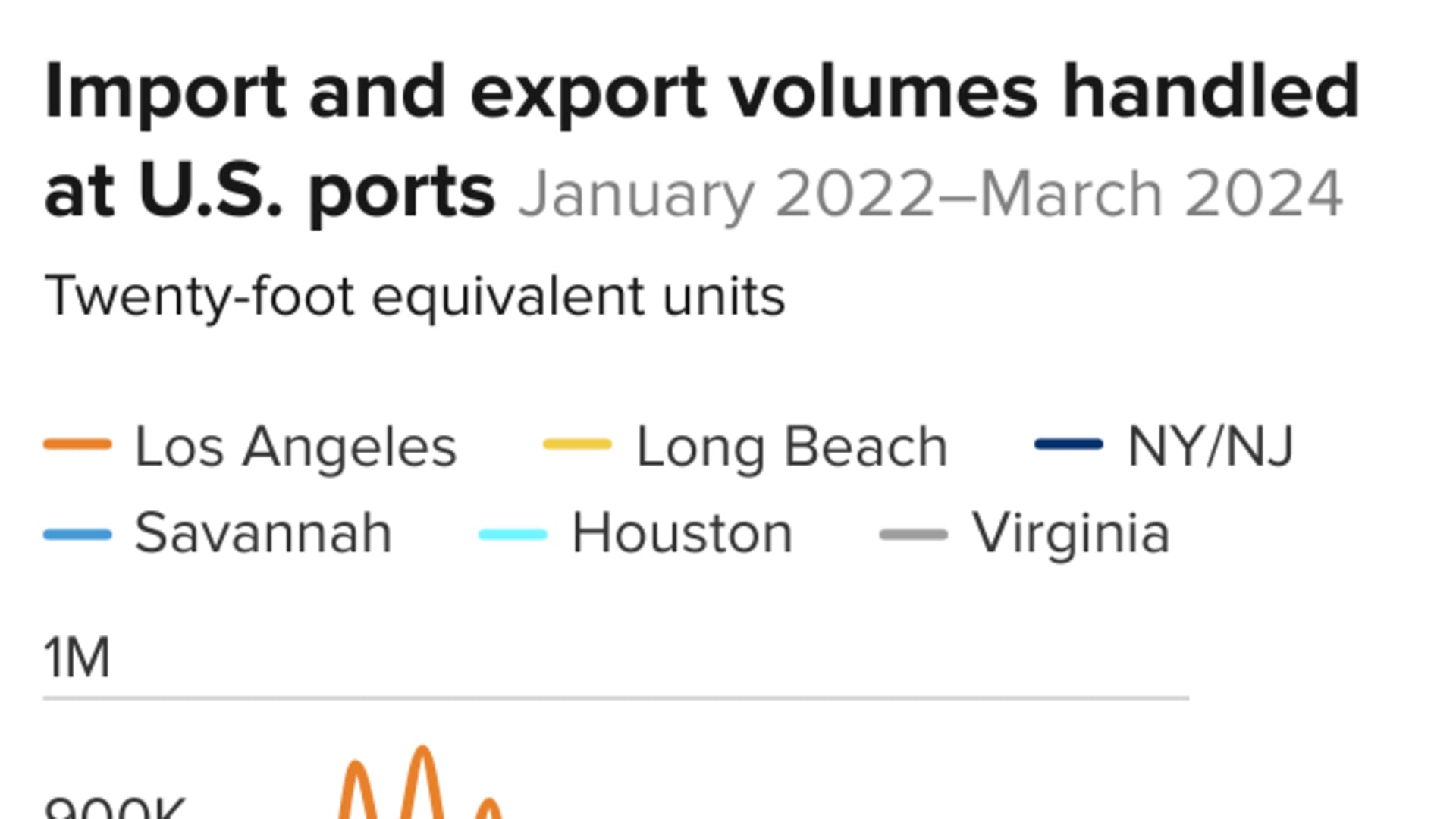
- The nation's largest ports are also at risk, and Biden administration cybersecurity officers and key port executives held a call on Wednesday to discuss security issues, including the Chinese-made cranes that have received government scrutiny this year.
- "More needs to be done across the ports, and supply chain," said Gene Seroka, executive director for the Port of Los Angeles, who noted that in 2023 the port stopped 750 million hacking attempts.
A top Biden cybersecurity official urged the nation's ports in a joint call on Wednesday to have their data encrypted, rapidly patch any vulnerabilities in critical systems, and have a well-trained cyber team as hacks targeting key U.S. infrastructure increase.
Anne Neuberger, Deputy National Security Advisor for Cyber and Emerging Technology, cited President Biden's signing in February of an executive order to strengthen the cybersecurity of U.S. ports. The nation's port system is the main point of entry for trade, employs 31 million people, and generates over $5.4 trillion for the U.S. economy.
"More needs to be done across the ports, and supply chain," said Port of Los Angeles executive director Gene Seroka, who has been fighting for years for a robust federal cybersecurity plan. "The executive order has elevated the discussion."
Get top local stories in Southern California delivered to you every morning. Sign up for NBC LA's News Headlines newsletter.
The first seaport in the United States to establish a Cyber Security Operations Center (CSOC) in 2014, the Port of Los Angeles, according to Seroka, fought the highest number of recorded cyberattacks against the port in 2023, with the CSOC stopping 750 million cyber intrusion attempts.
In a 2023 report, the Department of Transportation Maritime Administration warned that U.S. ports are vulnerable to cyber attacks due to the multiple stakeholders involved in the operation of the port, with risks identified related to facility access, terminal headquarters, operational technology systems such as communication systems and cargo handling equipment, positioning, navigation, and timing services, which would impact vessel movements and complex logistics systems at port facilities, and sharing between ships and ports of network connections and USB storage devices, among other technology.
Money Report
Neuberger, who advises Biden on cybersecurity, digital innovation, and emerging technologies, noted that the executive order has given the Coast Guard the ability to respond to attacks, instituted mandatory reporting of cyberthreats, and turning away ships that could pose national security danger.
One of the key areas of concern for the Biden administration and the executive order is the security of Chinese-manufactured cranes. Over 80% of all cranes operating at the ports in the United States are manufactured in China and some of the software used to operate those cranes is installed in China, which could compromise the crane's security, creating fears about a "trojan horse" for spying or controlling ports remotely.
Neuberger noted that ports can tap funds from the $1 trillion bipartisan infrastructure bill passed in 2021 to support the building of U.S. shipping cranes by a U.S. subsidiary of the Japanese industrial company Mitsui.
State-linked hackers attacking U.S. physical operations
Foreign hackers are increasingly targeting U.S. infrastructure across vital services, from transportation to food supply and health care. In February, the FBI warned Congress that Chinese hackers have burrowed deep into the United States' cyber infrastructure in an attempt to cause damage. FBI Director Christopher Wray said Chinese government hackers are targeting water treatment plans, the electrical grid, transportation systems and other critical infrastructure inside the U.S.
On Wednesday, Google's cybersecurity firm Mandiant released a report that included analysis of a Russian-linked hacking group and a January attack of a water filtration plant in a small Texas town, Muleshoe, where a water tank overflowed as a result of a cyber intrusion.
"The town may be small but it is located in an arid part of Texas and is near Cannon AFB in Clovis, New Mexico," said Adam Isles, head of cybersecurity practice for Chertoff Group, describing the location of the water filtration plant as "concerning."
In November of last year, US officials said Iran was behind a cyberattack at a Pennsylvania water plant. Biden administration officials recently warned the nation's governors about the threat to water systems. "Water is among the least mature in terms of security," Isles said.
The American Association of Port Authorities, which lobbies on behalf of the nation's major container ports, has said in the past there is no evidence to the support the remote control claims about Chinese-manufactured crane cyber vulnerabilities, characterizing the comments as "sensational."
When asked for an update on the review of the 200 plus cranes, Neuberger referred CNBC to the Coast Guard. In an email to CNBC, a Coast Guard spokesperson said that as of a few weeks ago, 92 of the more than 200 cranes manufactured in China were evaluated.
Public comments over the executive order's rulemaking began February 21 and will end on April 22.
Isles said it is important to identify the critical safety and business systems at the nation's ports.
"We can't protect everything, so you have to identify the high-value assets at the port," he said. "You need to identify what is central to operating a port or central to an adversary."
Isles says once the assets are identified, you need to have a continuous diagnosis of the operations and networks checking on their durability. "We need to assume these systems will be compromised at some point and need to address not only the minimal operating capacity but its resiliency and survivability. This helps achieve an offense-informed defense in cybersecurity," he said. Equally important, Isles stressed, is deterrence. "There needs to be accountability for offenders."
The ten-year anniversary of the Port of Los Angeles CSCO is in September. The CSOC currently monitors the port's own technology environment to prevent and detect cyber incidents, and it became the first port to achieve ISO 27001 information security management certification in 2015.
Activity at the Port of Los Angeles is picking up, with its first-quarter performance and March 2023 container activity released on Wednesday, and showing a 19% improvement in container volumes, and eight consecutive monthly periods of growth.
Correction: The Port of Los Angeles stopped 750 million hacking attempts in 2023. Due to an editing error, a previous version of this article misstated the figure in the article text.






